Watch out where you place your mobile number online.
SMS messages can be taken advantage of by unscrupulous online users and hackers, especially if they know the mobile number of the target.
There is an existing flaw in the manner that the social micro-blogging site manages SMS manages which posed the risk. Online hackers can tweet using the target?s own account as well as change profile and account information as long as they have the mobile phone number.
People who are particularly at risk include those who have enabled the feature that allows them to post messages on Twitter using SMS messaging after they registered the mobile phone number online.
The announcement was made by Jonathan Rudenberg (@titanous) through his blog post last December 5, 2012. According to Rudenberg, ?Twitter users with SMS enabled are vulnerable to an attack that allows anyone to post to their account.?
Rudenberg said that everyone should disable the SMS function and wait for Twitter to find a solution.
Rudenberg said he reported the risk to the company on August 17, 2012 and was advised not to divulge the information. He asked Twitter to provide updates two months later but to no avail. Before releasing his blog post, he told Twitter one last time that he needed to share the information for the benefit of online users.
One of the ways to prevent possible attacks is for Twitter users to take out their mobile phone numbers that are already registered on Twitter.
To do this, go to the Settings page to remove the input number. Online users should also be wary of the source or origin address of messages since hijackers can manipulate these by taking advantage of SMS gateways that let them gain access.
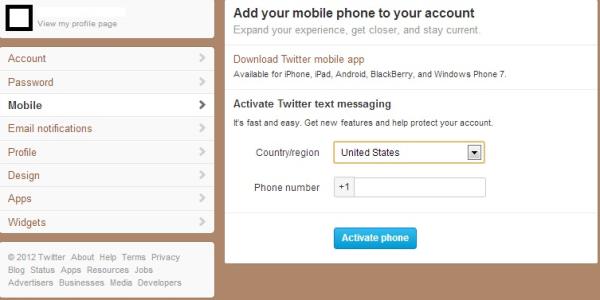 Another supposed means of protection is provided by Twitter, since the website has a prepared mechanism that will prevent the hijack. The problem is that the method is not available in America.
Some places that can be protected by the feature can set a PIN consisting of four digits to every SMS message to check if it is actually the account owner providing the commands. Those located outside the United States must activate the PIN quickly to stay protected.
After Rudenberg spread the news, he was emailed by Twitter that the flaw has already been fixed. On December 4, 2012, a representative from the company stated via email, ?Our team has already addressed this vulnerability.?
Another supposed means of protection is provided by Twitter, since the website has a prepared mechanism that will prevent the hijack. The problem is that the method is not available in America.
Some places that can be protected by the feature can set a PIN consisting of four digits to every SMS message to check if it is actually the account owner providing the commands. Those located outside the United States must activate the PIN quickly to stay protected.
After Rudenberg spread the news, he was emailed by Twitter that the flaw has already been fixed. On December 4, 2012, a representative from the company stated via email, ?Our team has already addressed this vulnerability.?
 Another supposed means of protection is provided by Twitter, since the website has a prepared mechanism that will prevent the hijack. The problem is that the method is not available in America.
Some places that can be protected by the feature can set a PIN consisting of four digits to every SMS message to check if it is actually the account owner providing the commands. Those located outside the United States must activate the PIN quickly to stay protected.
After Rudenberg spread the news, he was emailed by Twitter that the flaw has already been fixed. On December 4, 2012, a representative from the company stated via email, ?Our team has already addressed this vulnerability.?
Another supposed means of protection is provided by Twitter, since the website has a prepared mechanism that will prevent the hijack. The problem is that the method is not available in America.
Some places that can be protected by the feature can set a PIN consisting of four digits to every SMS message to check if it is actually the account owner providing the commands. Those located outside the United States must activate the PIN quickly to stay protected.
After Rudenberg spread the news, he was emailed by Twitter that the flaw has already been fixed. On December 4, 2012, a representative from the company stated via email, ?Our team has already addressed this vulnerability.?